What are the email security options? Part 3
18 Nov 2022 | Jindřich Zechmeister
In the third part of the series, we will look at email security from the user's point of view. What can you do for your communication security? For example, you will learn how to easily and effectively secure the entire company’s email automatically. And finally, we will introduce an effective anti-phishing weapon that can also help to improve email readability.
The S/MIME standard for mail security
S/MIME is the designation for the secure version of the MIME protocol, which is used as a common standard. S/MIME provides a guarantee of the communicators’ identity (using the person's data in the certificate), creates a digital seal for the message that protects it against changes, and enables full end-to-end encryption between the communicating parties.
To use S/MIME, you need a personal certificate that will be issued to the email address you will be communicating with. Then you can also sign and encrypt your messages. You can sign a message addressed to any recipient; thanks to the digital signature, they will know whether it arrived intact (without editing) and whether it came directly from you. If the addressee has your S/MIME certificate from a previous communication, you can also encrypt the message, which will protect it in the future when it is saved on the server. No one but you and the recipient will read the message.
It is obvious that for (meaningful) use of S/MIME you need to extend security across the entire company. You need to provide one S/MIME certificate for each user and it needs to be set up on the given computer, for example in Outlook. With a higher number of users, this is a tedious job and perhaps the main reason why S/MIME is not used in all companies. However, we know a solution for this problem as well.
KeyTalk (PKIaaS) fully automates S/MIME
Let's take a small detour to deploy S/MIME certificates in a corporate environment. Each certificate needs to be requested, confirmed and, after being issued to the user, set into the system (pair the private key with the issued certificate) and set for signing in the relevant programs.
This is not practically feasible with a higher number of users, because the administrator would have to check all the computers twice, taking many hours every year. Fortunately, there is a solution on the market that can automate these hardships and take care of (not only) personal certificates completely automatically. It's called KeyTalk.
KeyTalk is a Dutch company focusing on comprehensive PKI solutions. Their unique ManagedPKI server KeyTalk also offers as a cloud service Keytalk Secure Email Service (SES) (referred to as PKIaaS). Thanks to this, you can simplify S/MIME certificate deployment to the maximum.
If you are interested in learning more, please do not hesitate to contact us about KeyTalk. We will be happy to demonstrate it to you in practice.
User security with VMC/BIMI
In our series, we presented the technologies that contribute to the security of email use and that must be supported by the mail provider; only the S/MIME protocol is an exception and its security is available directly to the email user. VMC is a new feature that is set on the server, but primarily serves to secure the message’s recipient (addressee).
VMC and BIMI are the names of technologies that increase the security of email communication, mainly by the email recipient´s visual check. If you have a VMC certificate issued and a correctly set domain (BIMI), the recipient will see your company's logo (in selected clients and services). Simply using BIMI on a domain is not enough; to display the company logo, you also need a VMC certificate, which will be issued after both the logo and your company have been verified. Thanks to this, the email reader can trust the logo authentication (without the VMC certificate and verification, the logo could also be used by fraudsters).
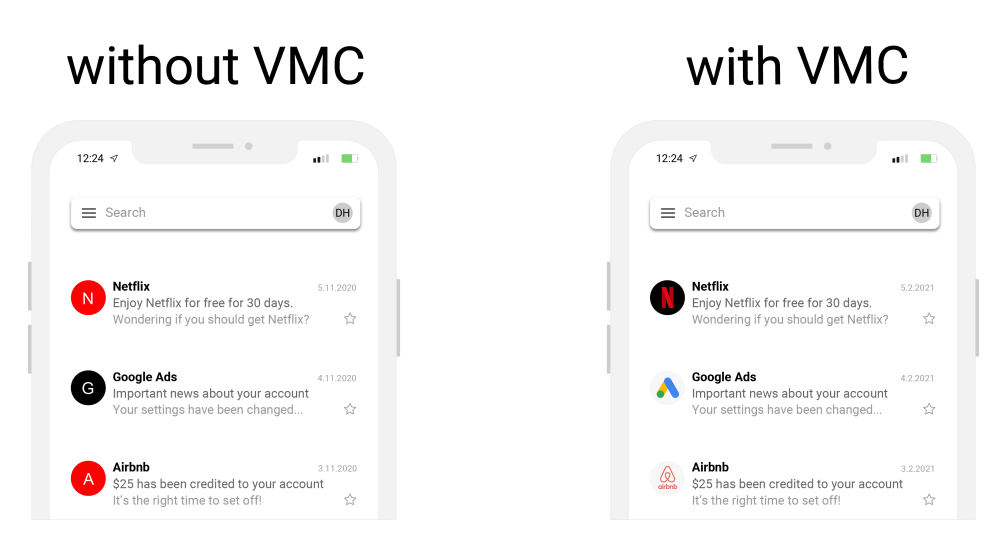
The identity of the VMC certificate applicant is checked by DigiCert and the right to use the logo is documented by an active trademark on it, so no one can abuse your company's logo. From a technical point of view, a functional VMC requires active DMARC on the sender's domain with a strict "reject" setting, thus protecting users from phishing with spoofed messages. If such a message was sent on behalf of your domain, the recipient will reject it and the domain administrator will see the message in the DMARC report summary and will know who tried to abuse it.
We will help you get a VMC certificate
SSLmarket will help you get and set up a VMC certificate for your business. We have prepared a summary of information that you should know before purchasing VMC certificates. However, you can purchase the certificate directly in the SSLmarket order. In this case, SSLmarket employees will contact you after receiving the order, as it will be necessary to agree on the details of the request.
TLS certificate specialist
Certificated Sales Expert Plus
e-mail: jindrich.zechmeister(at)zoner.com
